Settings
Global application settings are available under the Settings item of the main navigation menu.
The Settings page has the following sections:
Note: Application settings can only be accessed when logged in as the DataMasque admin user.
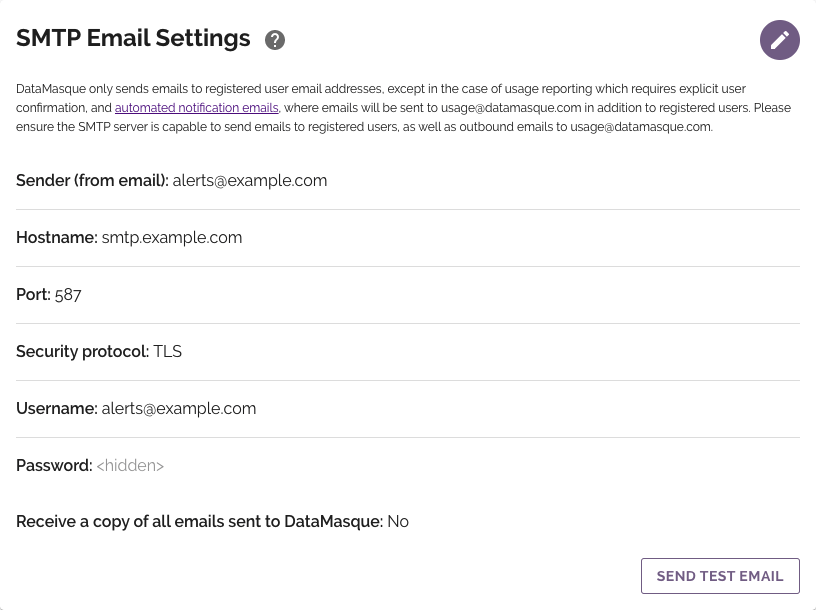
SMTP Email Settings
DataMasque can be configured to send emails over SMTP for the purposes of providing 'Forgotten Password' account recovery and critical system notifications. This will also be used to send support and usage information to DataMasque.
Note: Emails will be sent to usage@datamasque.com in addition to registered users. Please ensure the SMTP server is capable of sending emails to registered users, as well as outbound emails to usage@datamasque.com.
You can configure your SMTP server details by clicking the
![]() button. You will be presented with a
form to provide your configuration (see SMTP Parameters below for details):
button. You will be presented with a
form to provide your configuration (see SMTP Parameters below for details):
You may opt-in to receive a copy of any automated outbound emails that are sent to DataMasque HQ. This can be done by enabling the setting shown below.
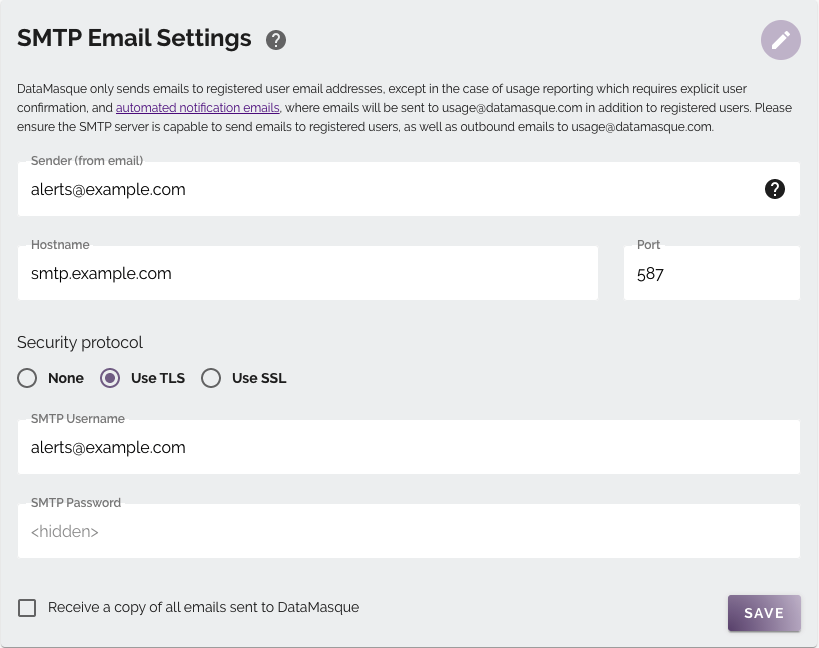
SMTP Parameters
| Sender | The email address that your DataMasque instance will send emails from* |
| Host Name | The hostname or IP address of your SMTP server (must be accessible from your DataMasque instance) |
| Port | The port used by your SMTP server |
| Security Protocol | The security protocol used by your SMTP server |
| SMTP Username | The username used to authenticate with your SMTP server (requires SSL or TLS) |
| SMTP Password | The password used to authenticate with your SMTP server (requires SSL or TLS) |
You can test saved SMTP server configurations by clicking the SEND TEST EMAIL button. This will send a test email to the email address associated with your user account to test connectivity to the specified SMTP server from DataMasque.
Note: Most non-relay SMTP servers that require SSL/TLS security protocol and SMTP credentials will rewrite the
Fromheader in messages to the corresponding SMTP account to secure the credentials of the sender. In that case, it is recommended to configure the SMTP credentials and DataMasqueSenderwith the same email address (for consistency).
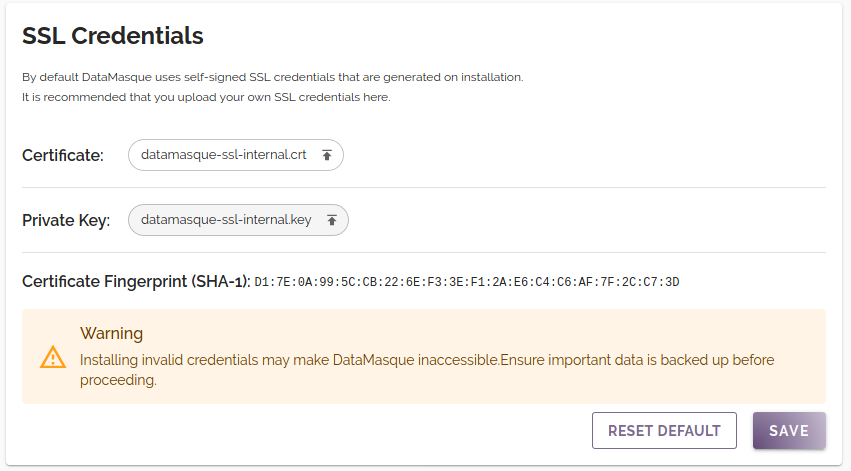
SSL Credentials
By default, DataMasque is configured with an auto-generated self-signed SSL certificate. The self-signed certificate must be accepted in the browser by a user when accessing DataMasque.
To ensure a secure SSL connection, it is recommended to install a certificate that has been signed by a trusted CA whose root certificate is installed on client machines.
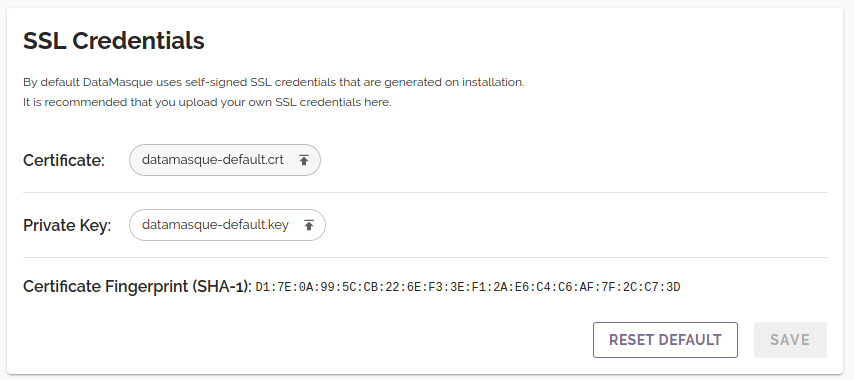
Active SSL Credentials
The SSL Credentials panel contains details of the SSL credentials currently in use by DataMasque, including the certificate and private key files and the SHA-1 fingerprint of the certificate:
Installing SSL Credentials
You are able to install your own SSL credentials using the "SSL Credentials" settings panel.
Note: DataMasque accepts X.509 SSL certificates in PEM format. Other formats are not supported.
Note: When generating an SSL certificate for DataMasque, it is recommended to correctly set the "Common Name" field to match the hostname of the DataMasque instance but also include SAN (Subject Alternative Name) entries that cover the potential IP addresses at which DataMasque may be accessed. In a Cohesity environment, this would include the IP address for each cluster node. This ensures that DataMasque can always be accessed using a secure connection.
New SSL certificate and private key files can be installed by clicking on each file and selecting replacements to upload. Before proceeding, ensure that any critical data stored in DataMasque is backed up. In the event that invalid or incorrect credentials are installed DataMasque may become inaccessible.
Once you are satisfied that you have backed up any important data, click the 'Save' button to update DataMasque with the selected credentials. After successful installation, your page will be refreshed to ensure that your browser is initialised with the new credentials.
If at any point you wish to revert to using the default self-signed SSL certificate, you may do so by clicking the "Reset Default" button.
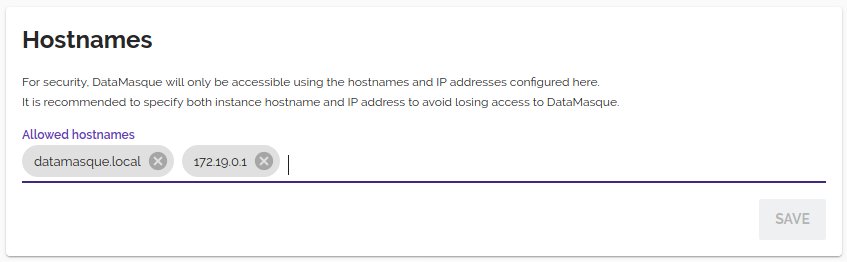
Hostnames
DataMasque must be configured with the hostnames and IP addresses that will be used to access the application. It is strongly recommended to include the DataMasque instance IP address in this configuration as well as hostname to avoid losing access to the application. Currently, only IPv4 addresses are supported.
Hostnames can be added and deleted using this interface, however deleting the hostname that is currently in use to access DataMasque is disallowed.
Instance Secret
Each DataMasque instance has a randomly generated instance secret to protect against attackers replicating deterministic masking on a different instance (see the deterministic masking guide for details). You can rotate the instance secret from the Settings page by clicking the Rotate Instance Secret button. After rotating the instance secret, subsequent deterministic masking will be based on a new instance secret, and existing rulesets will produce different masking results.
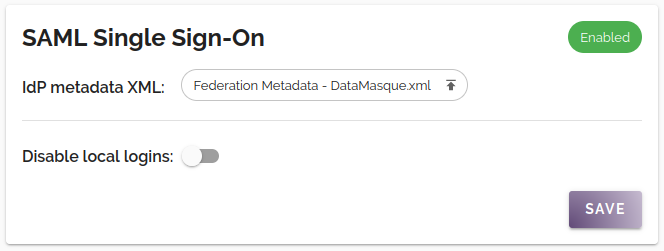
SAML Single Sign-On
The SAML Single Sign-On settings panel can be used to configure DataMasque for single sign-on (SSO). See the SAML Single Sign-On user guide for details about how SAML SSO works with DataMasque.
The following parameters can be configured for SAML SSO:
| IdP metadata XML | The SAML metadata XML file obtained from your identity provider. |
| Disable local logins | When SAML SSO is configured, enabling this will disable login of all local users (except the DataMasque admin user). |
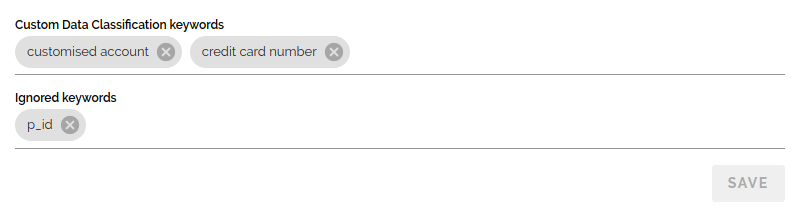
Global Keywords
You can provide DataMasque with Global Custom Data Classification keywords.
Column names are matched to Global Custom Data Classification keywords in addition to the built-in data discovery keywords.
Custom Data Classification keywords can be delimited by any number of spaces .
You can also provide DataMasque with Ignored keywords. Column names that match Ignored keywords are excluded from Sensitive Data Discovery reports.
Keywords can be added and deleted under the Global Keywords section on the Settings Page.
Example: regex:^street|postal, which matches any column name beginning with street or postal.
For more information please refer to our user guide on regular expressions
Patterns such as schema.table.column or schema.table are also supported for Custom Data Classification keywords and Ignored keywords,
but are not supported when prefixed by regex as . can also be used in regular expressions.
Wildcards are also supported by using the * character, for example you can discover or ignore all columns in any table by specifying schema_name.table_name.*